IoT Cybersecurity Engineering Services
From Threat Assessments to Vulnerability Monitoring
Trusted IoT cybersecurity services performed by experts and using security automation
Start with a Threat and Risk Assessment
A threat and risk assessment is a good place to start when considering cybersecurity for an IoT device. Whether the end application is automotive, consumer, medical, or industrial, a threat and risk assessment will help you determine the security controls you need. You don’t get extra credit for extra security!
BG Networks will help you through the process of identifying threats and how those threats translate to quantified risks. Once you have a ranked list of risks, you’ll be able to define security features (e.g., secure boot, encryption, IDPS) to make sure the highest priority risks are mitigated.
BG Networks can perform threat and risk assessments tailored to specific security standards, such as:
- ISO/SAE 21434
- FDA’s Refuse to Accept Policy
- ISA/IEC 62443
- Upcoming EU Cybersecurity Resilience Act
ISO/SAE 21434 Consulting Services
Security Assessments
BG Networks security assessment services can be applied to both existing and new IoT products. Assessment services offered include:
- Determination of cybersecurity relevancy
- Application of risk assessment methods
- Threat assessments
- Vulnerability assessments
- Development of cybersecurity goals, concepts, and requirements
- Assessment and recommendations for post-development key management and software signing
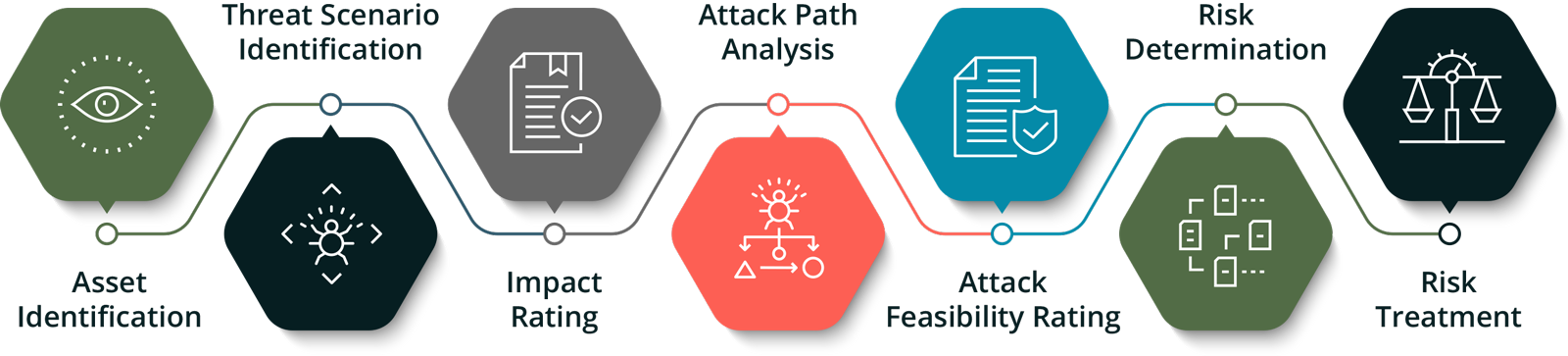
The diagram at the right shows the steps of a risk assessment approach that we can apply. We believe that IoT systems should only have the cybersecurity needed and not more. We will apply a risk assessment process to determine what cybersecurity controls are truly needed. We will even help determine how to treat the risks identified based on the risk tolerance of your business. Risk treatment options include mitigation, avoidance , transfer, or acceptance. For risks to be mitigated, we will help with the refinement of cybersecurity requirements and if needed, write the software to implement the identified cybersecurity features.
Markets that BG Networks is targeting for these security assessments services include automotive, medical, consumer, and industrial.
For automotive markets, BG Networks has a particular focus on is ISO/SAE 21434.
FDA Compliance Consulting Services
Cyber-Secure Software Embedded Software Development
Once a threat and risk assessment is completed, security requirements identified, and technical features specified, then the development and implementation can begin. BG Networks has an extensive background in implementing security features in IoT devices and embedded systems. The code that we will develop for you will use the hardware security features that are ubiquitous in microcontrollers and microprocessors, including:
- Hardware root of trust
- Secure boot
- Crypto accelerators
- Secure key storage
We have extensive experience implementing the features that have been identified as critical by organizations such as NIST, FDA, NHTSA, including:
- Multi-stage boot
- Firmware updates (OTA)
- Secure communications
- Trust Zone and Trusted Execution Environments (TEEs)
Security Testing
Once security features are implemented, the next step is to test. In addition to classical verification and validation testing, additional testing approaches are needed for security, including:
- Risk mitigation testing (similar to system level or validation testing)
- Penetration testing
- Bug bounty testing
The reason these additional test approaches are needed is to consider and test all threat vectors an adversary might exploit. As the saying goes, defenders need to be right all the time and the attacker only needs to be right once!
BG Networks can help with all of the above security testing, both in terms of services (i.e., we’ll do the testing for you) or providing tools that lower the cost of and reduce cybersecurity test time.
Automation Tools for Low-Cost Services
BG Networks also develops security automation tools. Often the original concept for these tools comes from the services we provide to improve efficiency.
Use of our automation tools enables us to provide the lowest cost services with the shortest possible schedules.
For example, BG Networks CRATE test platform automates testing, which shortens the time to run tests, including penetration tests on new releases of software.
Consideration of Standards, Laws, and Regulations
BG Networks can help you to comply to just about any standard, law, or regulations such as the EU’s R155 regulation for automotive cybersecurity and the FDA’s “Refuse to Accept” requirements for medical device cybersecurity. We can also ensure that our software development and testing services will comply with any public IoT cybersecurity standard that you need to meet.
QUESTIONS CONCERNING IOT CYBERSECURITY?
Commonly asked questions include:
- Do new laws and regulations apply to our products?
- Are our products cybersecurity relevant (i.e., should they include cybersecurity protections)?
- Does it make sense to perform a risk or threat assessment?
- Which standards or best practice recommendations make sense to consider?
- Some level of cybersecurity is required but which should be implemented?
- There’s not enough time to implement all the cybersecurity needed, what should we do?